Data protection has become a critical concern for every business owner. As cyber threats grow more sophisticated, the consequences of data breaches or unauthorized access become increasingly severe.
This article outlines practical recommendations to help safeguard your data, minimize risks, ensure your company's operational stability, and explain how Odoo protects your critical business information.
Why Data Protection Matters More Than Ever
Data drives business efficiency, decision-making accuracy, and customer trust. Any breach, hack, or accidental data loss can result in significant financial losses and damage to reputation. The volume of personal and commercial data continues to rise, with digital systems like ERP, CRM, and online services becoming central to business operations. This means that any vulnerability in business management systems can have serious repercussions.
Cybercriminals exploit technological access to employ advanced attack methods, and regulatory requirements for data protection are becoming stricter. Therefore, companies need robust mechanisms for access control, encryption, and data backup and recovery.
Given these circumstances, data security in ERP systems is paramount. Choosing a business management platform determines the level of protection for your most valuable asset—your information.
Major Business Threats in 2025
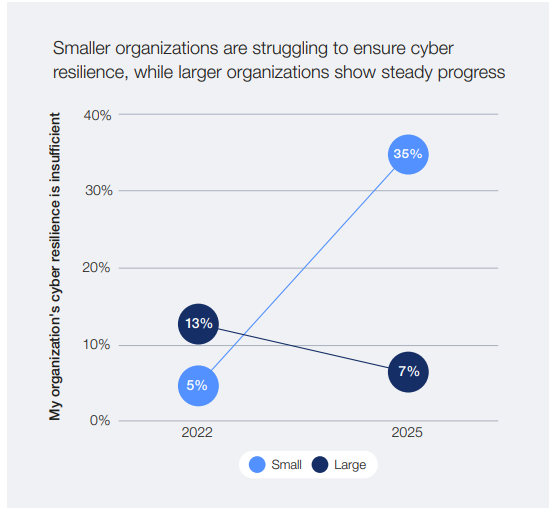
According to the “Global Cybersecurity Outlook” 2025 by the World Economic Forum in collaboration with Accenture, approximately 35% of small businesses believe their cyber resilience is inadequate – a figure that has increased sevenfold since 2022.
Sourse: World Economic Forum
The report identifies several factors contributing to cybersecurity challenges:
- Geopolitical tensions
- Cyber skill gaps
- Regulatory requirements
- Cybercriminal ingenuity
- Interdependencies in supply chains
- Artificial intelligence and emerging technologies

Sourse: World Economic Forum
What Data Should Businesses Protect?
It's crucial to identify the most vulnerable areas in your infrastructure, as not all data holds the same criticality. Priority should be given to data that directly impacts financial stability, reputation, and legal compliance.
Financial Information
This includes bank accounts, payment transactions, financial reports, budgets, and strategic financial plans. Unauthorized access or falsification of such data can lead to severe consequences, from direct financial losses to account freezes, reduced creditworthiness, and reputational damage.
Personal Data of Clients and Employees
This category encompasses names, contact information, passport and tax details, and, in some cases, medical information. Any breach of confidentiality can result in legal repercussions, including fines for violating GDPR and national legislation, as well as loss of trust from clients and partners.
Commercial and Operational Information
Data such as internal strategies, business plans, technological formulas, blueprints, supplier information, contracts, and collaboration terms often constitute the core of a company's competitiveness. A leak of this data can give competitors an advantage and jeopardize future developments, leading to breaches of partner agreements.
User Access and Permissions
Logins, passwords, tokens, and all tools that allow interaction with internal systems and databases. Improper management of these elements opens opportunities for both external attacks and internal security breaches. Clear access rights, regular audits, and multi-factor authentication significantly reduce the risk of unauthorized actions and data leaks.
The Verizon Data Breach Investigations Report 2025 found that stolen credentials were involved in 22% of all breaches, while 88% of web app attacks included the use of compromised accounts (Descope analysis of DBIR 2025). Poor password hygiene, shared credentials, and lack of multi-factor authentication are common pitfalls. Implementing RBAC, MFA, and regular access audits can dramatically reduce exposure to credential-based threats.
Integrations and Financial Services
This includes API keys, connections to banking systems, payment gateways, and interactions between ERP and other business applications. Compromise of these channels can lead to fraudulent transactions, loss of funds, or blocking access to critical services.
Explore More The Future of ERP: 9 Innovations Businesses Can’t Afford to Miss in 2026
How Odoo Protects Your Data
Odoo implements a comprehensive approach to data security, combining technological solutions, organizational practices, and compliance with international standards. This ensures reliable protection of client and user information. Key security measures include:
Architecture and Hosting
- Cloud Hosting: Odoo utilizes reputable cloud platforms such as Google Cloud and OVH.
- Data Center Certifications: Certifications like ISO 27001, SOC 1 TYPE II, SOC 2 TYPE II, PCI-DSS, CISPE, SecNumCloud, and CSA STAR confirm a high level of data storage security. For more details, in the official Odoo Security.
Encryption
- HTTPS and SSL: All data transmitted between users and servers is protected with 256-bit encryption.
- Disk Encryption: User data is encrypted on servers, safeguarding it even in the event of physical access to hardware.
Authentication and Access Control
- Two-Factor Authentication (2FA): Adds an extra layer of security during login.
- Flexible Roles and Permissions: Ensures minimal user privileges and restricts access to sensitive information.
- User Activity Audit: Activity logs allow tracking of changes and data access, enhancing transparency and helping detect anomalies.
Backup
- Automatic Daily Backups: Ensures data preservation in unforeseen situations.
- Data Recovery with a Few Clicks: Users can quickly restore information through the Odoo interface.
Updates and Patches
- Regular Security Updates: Fix vulnerabilities and enhance system protection.
- Automatic Patch Application: Enables prompt response to new threats.
Secure Development and Modules
- Third-Party Module Verification: Modules undergo security compliance checks before being published in the Odoo Apps Store.
- Best Practices in Development: Adherence to OWASP Top 10 and code reviews ensure high-level security in programming code.
Compliance with International Standards
- GDPR: Odoo processes personal data only under client instructions, notifies about unauthorized access, and provides options to edit or delete data (Odoo GDPR).
- Privacy Policy: Defines rules for data collection, processing, and protection (Odoo Privacy Policy).
- Other Certifications: ISO/IEC 27001, SOC 2, and compliance with local requirements.
Third-Party Service Usage Policy
- Third-Party Collaborations: Odoo partners with third parties for payment processing and analytics, ensuring their compliance with data protection standards. (Odoo Acceptable Use Policy)
Employee Training and Awareness
Odoo places significant emphasis on continuous improvement of its employees' awareness regarding data security and confidentiality.
Key elements of the program include:
- Continuous Training. Employees undergo regular interactive training sessions, including quizzes, assessments, and phishing attack simulations.
- Individual Development. Each employee is entitled to 12 days of personal training through internal and external programs covering cybersecurity, management, communication, and other professional skills.
- Specialized Training for Developers. The Odoo Security team conducts practical training on internal security, focusing on vulnerability analysis in technologies used within Odoo. This enables employees to acquire cybersecurity skills directly related to their activities.
Through this system, Odoo maintains a high level of staff awareness and minimizes risks associated with the human factor, often the weakest link in data protection.
Related Articles How to Set Up User Access in Odoo to Protect Your Data
Final Thoughts
In short, protecting your business data is no longer optional. With Odoo’s robust security measures, including encryption, access controls, backups, and continuous compliance, you can safeguard critical information, minimize risks, and focus on growing your business with confidence.
